This is an old revision of the document!
Table of Contents
Remote Access to your Workstation
For security reasons, access to your Lorentz workstation is only possible within the Lorentz Institute sub-network. Remote access can occur either securing your connection via an intermediate step called SSH tunneling (AKA port forwarding) or through the Lorentz Institute VPN service.
SSH tunneling
By means of an SSH tunnel you can transport any arbitrary data over an encrypted SSH connection. Members of the Lorentz Institute can use this technique to gain remote shell access to their workstation across our firewall which would prevent access otherwise.
How does it work?
| You must have an ssh client installed on your personal device – e.g. laptop, PC – in order to establish a tunnelled connection. |
| The Lorentz Institute has a dedicated server (SSH server) ready to listen to any (authenticated) client connections. |
| Once a client-server connection is established, a given application contacts the SSH client on a chosen port on which the client is listening. |
| The SSH client in turns forwards all encrypted application data to the server which finally communicates with the actual application server. |
For remote ssh connections to your IL workstation, the steps above can be summarised into the following. Establish an ssh client-server to our SSH server and instruct your SSH client to forward any new SSH-connection data that will be sent to an arbitrary port number to go via our SSH server. The server will then relay this information to the SSH server running on your workstation.
Here follows a few examples to help you get started.
Example 1
Should you want to open an ssh session to your workstation and you are located outside the Lorentz network you can tunnel your request through ssh.lorentz.leidenuniv.nl. For example
ssh -f <your_username>@ssh.lorentz.leidenuniv.nl -L 2222:<your_workstation>.lorentz.leidenuniv.nl:22 -N
instructs your machine to `tunnel' requests to local port 2222 through ssh.lorentz.leidenuniv.nl to finally reach port 22 (sshd) on your workstation. Use ps to see if the command above executed successfully
ps aux | grep ss[h] your_username 6217 0.0 0.0 89612 2948 ? Ss 13:19 0:00 ssh -f your_username@ssh.lorentz.leidenuniv.nl -L 2222:your_workstation.lorentz.leidenuniv.nl:22 -N
At this point you are ready to initiate an ssh session to your workstation
ssh -p 2222 localhost
NOTE: Should you want ssh to set the DISPLAY environment variable, you can use option -X when you run ssh. You can invoke the ssh manual pages by typing man ssh.
Example 2
Case scenario: you are at home and you would like to connect to your workstation named `asselijn'.
Locally (e.g. on your laptop), create a file .ssh/config with a section for the machine to which you want to log in, containing the ProxyCommand ssh option to do the tunnelling:
Host asselijn.lorentz.leidenuniv.nl asselijn
ProxyCommand /usr/bin/ssh -W %h:%p ssh.lorentz.leidenuniv.nl
And if you have a different username locally and on the institute desktops, that can be added like this:
Host asselijn.lorentz.leidenuniv.nl asselijn
ProxyCommand /usr/bin/ssh -W %h:%p username@ssh.lorentz.leidenuniv.nl
User username
If you need access to multiple hosts, just copy and edit the example above.
Once this configuration is in place, a simple ssh asselijn will get you to the machine you have configured.
Example 3

You sit in your office at the IL and have started a jupyter notebook on marisXX port YYYY. To connect to your notebook using the browser on your workstation you must tunnel through `xmaris'. Edit your local .ssh/config
Host maris HostName xmaris.lorentz.leidenuniv.nl LocalForward YYYY localhost:YYYY Host marisXX HostName marisXX ProxyJump maris LocalForward YYYY localhost:YYYY
You are now ready to tunnel your connections through xmaris and visualize your notebook at http://localhost:YYYY.
NOTE: For this to work your workstation must have OpenSSH v7.3+.
Example 4

Same situation as in Example 3 but this time you sit behind your laptop at home.
Host lorentz
HostName ssh.lorentz.leidenuniv.nl
User <your-IL-username>
IdentityFile ~/.ssh/id_rsa
Host maris
HostName xmaris.lorentz.leidenuniv.nl
ProxyJump lorentz
IdentityFile ~/.ssh/id_rsa
User <your-IL-username>
Host marisXX
HostName marisXX.lorentz.leidenuniv.nl
ProxyJump maris
IdentityFile ~/.ssh/id_rsa
User <your-IL-username>
LocalForward YYYY localhost:YYYY
Example 5: Using Putty

novamaris with xmaris.
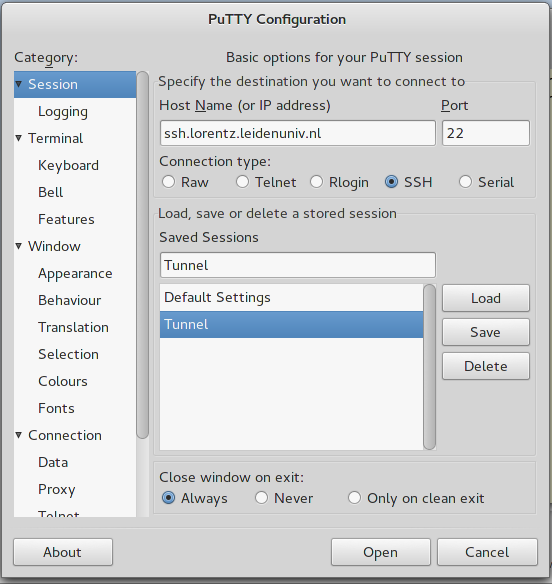
You will need to open two putty sessions. The first one opens a tunnel, the second one uses it. For the sake of clarity let us call the first session `Tunnel' and the second one `Tunnel_use'. In this example we will establish a connection to the Maris headnode novamaris through an ssh tunnel on ssh.lorentz.leidenuniv.nl.
Session 1: Tunnel
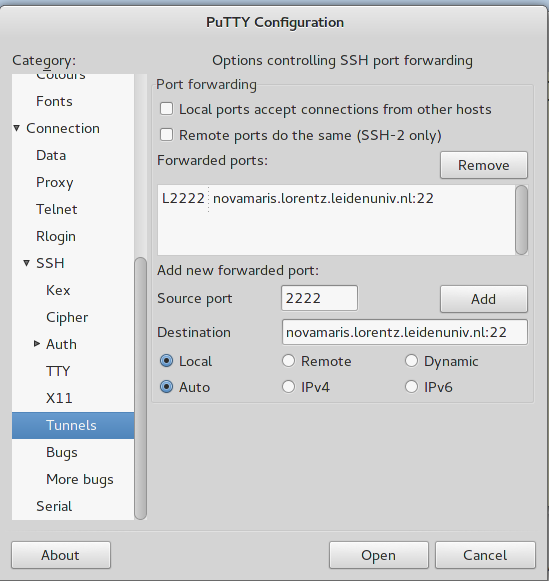
Open putty and create a session called Tunnel, then set it according to the snapshots below
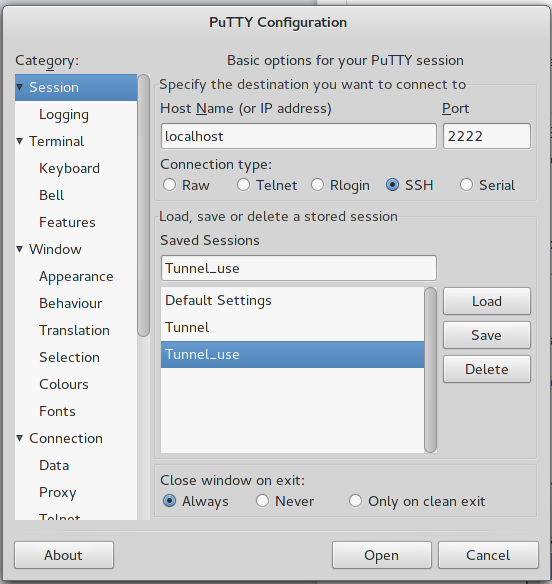
Please note the settings in the port forwarding panel. We use an arbitrary port (2222), but you can choose any numbers above 1024 provided they are not currently in use. By pushing `Open', a terminal will appear so that you can authenticate using your Lorentz institute credentials. Leave this terminal open and proceed with the creation of session `Tunnel_use'
Now push `Open' and a terminal will appear asking your authentication credentials on novamaris. Any other putty connection to localhost:2222 will ssh directly to novamaris.
VNC: GNU/Linux
For detailed instructions on how to set up a vnc session you are encouraged to follow these instructions.
Finally, take a look at x2go should you be interested.
VNC: Windows Users
Please read here.
Proxy Browsing
Read here